This is a "this has never happened to me before" post.
I have an internal DVD-RAM drive (
DVD Recorder, multi-foremat) and when I opened
My Computer I noticed that it was missing. All my other drives (
internal and external) did show.
I've had this DVD drive for years with no problems.
So, what to check:- Rebooted and checked BIOS to see the DVD drive listed
- Used Device Manager, under DVD/CD-ROM drives to see list (see screenshot)
My
HP DVD Writer was listed in both places.
Normally this drive was listed as
G: but there was no such drive in
My Computer.
Solution:Open
Disk Management (
in Computer Management) and scroll-down to where your CDs are shown in the right (
see screenshot).
Each drive SHOULD have a Logical Drive Letter assigned.I found that one CD/DVD drive had no
Logical Drive Letter.
You right-click on the drive on the right panel, select
Change Change Drive Letter and...., then (
in this case) [Add] a drive letter. The dialog will show the next available letter.
In this case it showed
G: which is what my
HP DVD Writer should have been. Clicked [OK] and my DVD displayed AFTER I closed
Computer Management.
(click for better view)
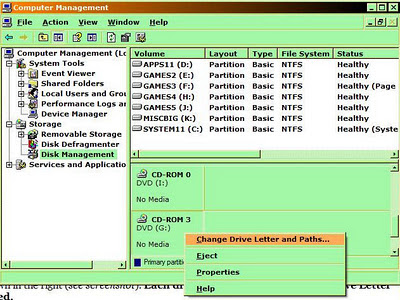
Note that this screenshot was taken AFTER I reassigned my
HP DVD Writer as G:, and
CD-ROM 0 is actually my external DVD-Recorder.