 |
| (Right-hand Pic edited to my arrangement) |

My old Android (
Google) was dying, so I just got an Apple
iPhone 6 iOS9.
I found out that
if you are running iOS9, Android has a
Move from Android to iPhone app.
This made getting all my data (
contacts, pictures, etc.) transferred to my iPhone easy.
It is a very nice smartphone, but it took me about 20hrs tinkering to get it the way I wanted it. Then there's the cost (
don't ask) even though I use
Consumer Cellular which provides low cost phones, no-contract account, and you customize you plan. Also give AARP discounts, which is great for us 70-somethings.
The madding thing is
Apple insisting in forcing you to use
iTunes to upload/sync anything. I had a very @#!@@#! time figuring out how to get my ringtones on the iPhone. In fact, it's iTunes that loads the driver so you can see you iPhone on your PC.
Finally found a
YouTube video on how to do that, but if you watch it you'll see it is complicated. But its better than trying any sync/download app to work as advertised.
UPDATE: There are some mistakes in the above video, the author seems to be using an older version of iTunes. Also there is a ringtone download site that you can use to get ringtones in the correct
.m4r format.
ZEDGE Ringtones (
screenshots below)
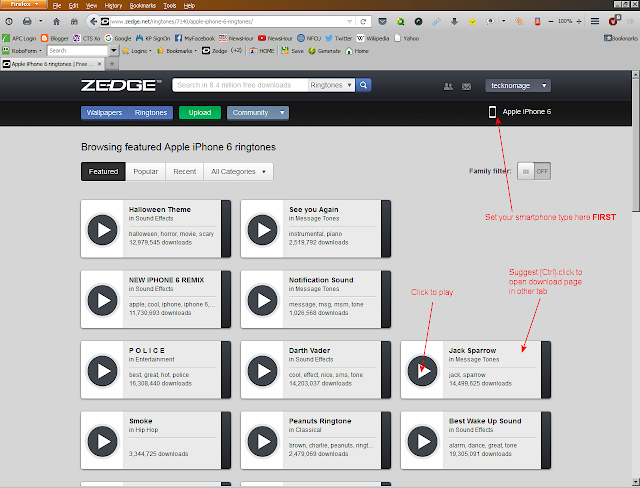 |
| Home Page for my iPhone |
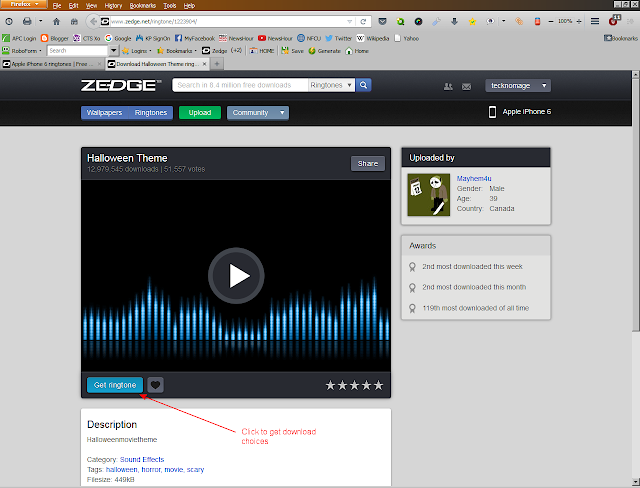 |
| Example Download page |
I suggest you download to your computer so you can drag-drop to iTunes, therefore be available for new phones. On my Win7 Pro 64bit rig, downloads go to the
Downloads folder, do drag/drop to iTunes is easy. Since the downloaded files are ringtone-ready, no need to go through the complicated steps of creating
.m4r files.
CORRECTIONS: Here are screen shots for newer versions of iTunes you need.
There were several sites that helped, here's two:
So far, I do like
iPhone 6 iOS9..... so far.



















