News of game-related hacks are nothing new; they have dominated headlines in recent years, from the massive Sony PlayStation Network takedown to the more recent hack of The War Z.
Attacks on gaming firms might not be isolated incidents, however. Researchers at Kaspersky Lab this week said they uncovered a series of targeted attacks originating in China that are taking aim at Web-based gaming companies.
"According to our estimations, this group has been active for several years and specializes in cyber attacks against the online video game industry," Kaspersky said in a blog post. "The group's main objective is to steal source codes for online game projects as well as the digital certificates of legitimate software vendors. In addition, they are very interested in how network infrastructure (including the production of gaming servers) is set up, and new developments such as conceptual ideas, design and more."
Kaspersky started investigating the group - known as Winnti - in the fall of 2011 at a behest of a computer game publisher that detected malware on its network. The malware was pushed out to users via a standard update, prompting concern that the company was spying on its users.
"However, it later became clear that the malicious program ended up on the users' computers by mistake; the cybercriminals were in fact targeting the companies that develop and release computer games," Kaspersky said.
Once installed on someone's computer, the hackers could control that machine without the user's knowledge. The malware was "the first time we saw Trojan applications for the 64-bit version of Microsoft Windows with a valid digital signature," Kaspersky said. Previous incidents of digital signature abuse had only hit 32-bit systems.
The digital certificate in question belonged to South Korea-based KOG, which also produced MMPRG, like Kaspersky's client. Ultimately, the certificate was revoked, but "over the next 18 months we discovered more than a dozen similar compromised digital certificates."
Kaspersky said that its research suggests that at least 35 companies from around the world have been infected by Winnti malware at some point in time, with a "strong focus" on Southeast Asia.
Showing posts with label networking. Show all posts
Showing posts with label networking. Show all posts
Friday, April 12, 2013
SECURITY - Online Gaming Firms Targeted by Malware
"'Winnti' Malware Targeting Online Gaming Firms" by Chloe Albanesius, PC Magazine 4/12/2013
Labels:
cybersecurity,
malware,
networking,
pc security,
trojan
Friday, February 1, 2013
CYBERWAR - New York Times Hacked by China
"New York Times Computer System Target of Lengthy Chinese Hacking Attack" PBS Newshour 1/31/2013
Excerpt
Excerpt
SUMMARY: The New York Times fell victim to a four-month cyber attack by Chinese hackers who cracked passwords to more than 50 email accounts, including those of top reporters. Ray Suarez talks with Times reporter Nicole Perlroth and Grady Summers, vice president of the cyber security company hired to investigate the attacks.
Labels:
cybersecurity,
data security,
networking,
web
Wednesday, May 30, 2012
CYBERSECURITY - Cyber Wars' Latest
"Sophisticated Virus Infects Computers in Iran, Mideast" by FARNAZ FASSIHI And PAUL SONNE, Wall Street Journal 5/29/2012
Thousands of computers in Iran belonging to government agencies and private companies have been infected with a highly sophisticated virus, dubbed Flame, in the latest cyberstrike against the Islamic Republic, said cybersecurity experts and Iran's telecommunications ministry.
The malware was widely detected across the Middle East in Syria, Israel and the Palestinian Authority, as well as in other parts of the world, but Iran has the largest number of infected computers, experts said.
At least three times since 2010, Iran has been targeted with sophisticated computer viruses such as Stuxnet, Duqu and Wiper. These viruses have disabled centrifuges for enriching uranium, stolen data from nuclear facilities and erased computers at the oil ministry.
The aim of Flame, said experts at Kaspersky Lab, a Russian information-technology security firm that reported the virus on Monday, was espionage, not physical damage or system interruption.
Flame, which Kaspersky said has been in operation since March 2010, was still active as of Monday morning, Alexander Gostev of Kaspersky Lab said. But after Kaspersky reported the existence of the virus publicly, Flame's operators immediately set about shutting the servers, an effort to protect the stolen data and hide the source of the virus. By Tuesday, Flame had become inactive, he said. "They are trying to hide."
The creation and operation of the Flame virus must have required a large staff, Mr. Gostev said. He estimated that at least 20 specialists would have been required to create and maintain the cyberweapon, similar to estimates of how many people invented and worked on Stuxnet.
Independent security experts said the scope of its complexity and method of operation suggests Flame was sponsored by a nation-state. It wouldn't be economically feasible, they argued, for a private corporation to run such a large-scale international cyberattack. Another reason a state is suspected is that the virus is designed to gather information but has no clear monetizing function.
Iran on Tuesday said it was a victim of cyberwarfare by Israel and the U.S., the semiofficial Fars news agency reported.
"It's in the nature of some countries and illegitimate regimes to spread viruses and harm other countries. We hope these viruses dry out," Ramin Mehmanparast, Iran's Foreign Ministry spokesman, said on Tuesday.
Iran's computer emergency response team, known as Maher, a branch of the telecommunication ministry, said on Tuesday that it was sharing research information on the virus for the first time ever on its website. Maher posted a link to antivirus software developed by its researchers to remove Flame and offered assistance to any infected organization.
Maher also said Flame was linked to an earlier cyberattack that erased data. In March, Wiper disrupted internal Internet communications at Iran's oil ministry and stole massive amounts of data.
Flame is the biggest and most high-functioning cyberweapon ever discovered, various cybersecurity experts said. It is comprised of multiple files that are 20 times larger than Stuxnet and carry about 100 times more code than a basic virus, experts said.
The most alarming feature, experts said, is that Flame can be highly versatile, depending on instructions by its controller. The malware can steal data and social-network conversations, take snapshots of computer screens, penetrate across networks, turn on a computer's microphone to record audio and scan for Bluetooth-active devices.
The cyber espionage activities described by the researchers are cyberspying techniques employed by the U.S., Israel and a number of other countries, cybersecurity specialists said. Cybersecurity researchers said the complexity of Flame's coding and comprehensiveness of its spy capabilities could suggest it was the work of a government.
Experts said they believe Flame reports back the information to a central command-and-control network that has constantly changed location. Analysts found servers in Germany, Vietnam, Turkey, Italy and elsewhere, but haven't located the main server.
White House National Security Council spokeswoman Caitlin Hayden declined to comment on Iranian accusations of U.S. involvement.
Analysts suspected Israel and the U.S. to be behind Stuxnet, but the link hasn't been confirmed. U.S. officials have declined to comment on Stuxnet's origins, but former U.S. officials said they regard it as a joint effort between the U.S. and Israel. That virus infected computers in several countries but was written to only sabotage specific systems in Iran, they said.
Stuxnet's purpose differed considerably from the apparent aim of Flame. Stuxnet was designed to damage computerized control systems running nuclear centrifuges, while Flame appears to have been designed for high-end targeted espionage. Researchers haven't found evidence of any damage to systems caused by Flame.
Israel has neither confirmed nor denied being involved with Stuxnet.
On Tuesday, Deputy Prime Minister Moshe Ya'Alon hinted that the country may be involved in Flame, saying in an interview with Army Radio, "Anyone who sees the Iranian threat as a significant threat—it's reasonable [to assume] that he will take various steps, including these, to harm it."
U.S. officials draw a distinction between cyber espionage and cyberattacks, which have a destructive or manipulative purpose and could be considered an act of war.
"We have strong beliefs that there are nations behind this malware. We assume it's related to the regimes and political situation in the Middle East," said Vitaly Kamluk, the chief malware expert for Kaspersky Lab.
Independent experts have been on the virus's trail for about a month. The International Telecommunications Union, the special agency at the United Nations that coordinates cybersecurity efforts, approached Kaspersky Lab in late April to investigate a series of incidents tied to a malware program known as Wiper. In the process of that investigation, the experts discovered Flame.
Iran's Supreme Leader Ayatollah Ali Khamenei has called the Internet a threat to national security and a dangerous double-edged knife that has benefits as well as risks.
Since 2009, Mr. Khamenei has instructed security forces to train and form units to battle cyberattacks to curb the influence of social-media websites.
In March, Mr. Khamenei issued a decree ordering the creation of the Supreme Council of Cyberspace, a committee consisting of high-level military and intelligence officials tasked with supervising cyber activity and warfare.
Labels:
computer worms virus,
cybersecurity,
internet,
networking
Tuesday, September 13, 2011
CYBERSECURITY - Internet WEB Threat
"Hacker Rattles Security Circles" by SOMINI SENGUPTA, New York Times 9/11/2011
Excerpt
Excerpt
He claims to be 21 years old, a student of software engineering in Tehran who reveres Ayatollah Ali Khamenei and despises dissidents in his country.
He sneaked into the computer systems of a security firm on the outskirts of Amsterdam. He created fake credentials that could allow someone to snoop on Internet connections that appeared to be secure. He then shared that bounty with people he declines to name.
The fruits of his labor are believed to have been used to tap into the online communications of as many as 300,000 unsuspecting Iranians this summer. What’s more, he punched a hole in an online security mechanism that is trusted by millions of Internet users all over the world.
Comodohacker, as he calls himself, insists he acted on his own and is unperturbed by the notion that his work may have been used to spy on antigovernment compatriots.
“I’m totally independent,” he said in an e-mail exchange with The New York Times. “I just share my findings with some people in Iran. They are free to do anything they want with my findings and things I share with them, but I’m not responsible.”
In the annals of Internet attacks, this is likely to go down as a moment of reckoning. For activists, it shows the downside of using online tools to organize: an opponent with enough determination and resources just might find a way to track their every move.
It also calls into question the reliability of a basic system of trust that global Internet brands like Google and Facebook, along with their users, rely upon. The system is intended to verify the authenticity of a particular Web site — to ensure, in effect, that Gmail is Gmail, and that the connection to the site is encrypted and difficult for an outsider to monitor.
Hundreds of companies and government authorities around the world, including in the United States and China, have the power to issue the digital certificates that the system relies upon to verify a site’s identity. The same hacker is believed to be responsible for attacks on three such companies.
In March, he claimed credit for a breach of Comodo, in Italy. In late August came the attack on the Dutch company DigiNotar. On Friday evening, a company called GlobalSign said it had detected an intrusion into its Web site, but not into more confidential systems.
Armed with certificates stolen from companies like these, someone with control over an Internet service provider, like the Iranian authorities, could trick Internet users into thinking they were safely connected to a familiar site, while eavesdropping on their online activity.
Fearing the prospect of other breaches similar to those carried out by this hacker, Mozilla, the maker of the Firefox Web browser, last week issued a warning to certificate authority companies to audit their security systems or risk being booted off Firefox.
“It is a real example of a weakness in security infrastructure that many people assumed was trustworthy,” said Richard Bejtlich, the chief security officer of Mandiant Security in Alexandria, Va. “It’s a reminder that it is only as trustworthy as the companies that make up the system. There are bound to be some that can’t protect their infrastructure, and you have results like this.”
Labels:
Cybercrime,
cybersecurity,
data security,
networking,
pc security
Thursday, July 28, 2011
SECURITY - Cybercrime, Attacker Arrested
"British Police Make Arrest in Net Attacks" by SOMINI SENGUPTA, New York Times 7/27/2011
Excerpt
Excerpt
The British police announced the arrest on Wednesday of a 19-year-old man who they said was the spokesman of the online vigilante group Lulz Security, which has claimed responsibility for a string of attacks on the Web sites of government agencies and private corporations.
In a statement, the police said the man used the online alias Topiary and had been picked up during a raid on a residence in the Shetland Islands, the rugged archipelago off the northeastern coast of Scotland. The police said they were also questioning a 17-year-old but had not arrested him.
On Twitter, Topiary described himself as a “simple prankster turned swank garden hedge.” His missives were often facetious, suggesting the handiwork of someone who relished playful language.
Lulz Security, the offshoot of a larger and more amorphous hacker group called Anonymous, has said it was responsible for attacks on the sites of PBS, the Senate, the Arizona Department of Public Safety and a company associated with the F.B.I.
Labels:
Cybercrime,
data security,
networking,
pc security
Thursday, January 6, 2011
TECHNOLOGY - Better Wired Brains?
PBS Newshour 1/5/2011
Excerpt from transcript
MILES O'BRIEN (Newshour): It is seductive, no matter what the age, but is it efficient? Can we really multitask?
Well, yes, with a caveat.
MARCEL JUST, Carnegie Mellon University: We can do it, but at tremendous cost. You can't do two tasks as well as you can do each one separately.
MILES O'BRIEN: Neuroscientist Marcel Just is doing some groundbreaking research on the human brain at Carnegie Mellon University.
So, we pay a big penalty for doing more, two things at once?
MARCEL JUST: That's right. There's only so much brain capability at any one time, throughput. And you can divide it down as much as you want to, but the price will be even higher then.
MILES O'BRIEN: Like driving and talking on the phone. A few years ago, Just did a study on this. His conclusion? Even an idle conversation takes a 40 percent bite out of your brainpower. You might as well be drunk.
So, multitasking is not a myth, but efficient multitasking might be?
MARCEL JUST: Yes. Multitasking with no cost is a myth. I think there's no free lunch there.
Labels:
networking,
technology
Tuesday, December 21, 2010
NETWORK - Internet Access, NET Neutrality
"F.C.C. Is Set to Regulate Net Access" by BRIAN STELTER, New York Times 12/20/2010
Excerpt
UPDATE
"F.C.C. Approves Net Rules and Braces for Fight" by BRIAN STELTER, New York Times 12/21/2010
Excerpt
Excerpt
The Federal Communications Commission appears poised to pass a controversial set of rules that broadly create two classes of Internet access, one for fixed-line providers and the other for the wireless Net.
The proposed rules of the online road would prevent fixed-line broadband providers like Comcast and Qwest from blocking access to sites and applications. The rules, however, would allow wireless companies more latitude in putting limits on access to services and applications.
Before a vote set for Tuesday, two Democratic commissioners said Monday that they would back the rules proposed by the F.C.C. chairman, Julius Genachowski, which try to satisfy both sides in the protracted debate over so-called network neutrality. But analysts said the debate would soon resume in the courts, as challenges to the rules are expected in the months to come.
Net neutrality, broadly speaking, is an effort to ensure equal access to Web sites and cutting-edge online services. Mr. Genachowski said these proposed rules aimed to both encourage Internet innovation and protect consumers from abuses.
“These rules fulfill a promise to the future — to companies that don’t yet exist, and the entrepreneurs that haven’t yet started work in their dorm rooms or garages,” Mr. Genachowski said in remarks prepared for the commission’s meeting on Tuesday in Washington. At present, there are no enforceable rules “to protect basic Internet values,” he added.
Many Internet providers, developers and venture capitalists have indicated that they would accept the proposal by Mr. Genachowski, which Rebecca Arbogast, a regulatory analyst for Stifel Nicolaus, a financial services firm, said “is by definition a compromise.”
UPDATE
"F.C.C. Approves Net Rules and Braces for Fight" by BRIAN STELTER, New York Times 12/21/2010
Excerpt
Want to watch hours of YouTube videos or sort through Facebook photos on the computer? Your Internet providers would be forbidden from blocking you under rules approved by the Federal Communications Commission on Tuesday. But if you want to do the same on your cellphone, you may not have the same protections.
The debate over the rules, intended to preserve open access to the Internet, seems to have resulted in a classic Washington solution — the kind that pleases no one on either side of the issue. Verizon and other service providers would prefer no government involvement. Public interest advocates think the rules stop far short of ensuring free speech.
Labels:
FCC,
net neutrality,
networking,
web
Tuesday, December 14, 2010
SECURITY - User's Bad Habits
PBS Newshour 12/13/2010
Excerpts from transcript
JEFFREY BROWN (Newshour): All right, we talk about this group called Gnosis. How much do we know about what -- who they are? And what did they do to Gawker?
HARI SREENIVASAN, staff writer, Wired.com: Well, a lot of these sort of hacker groups are very shadowy in nature, in the sense that they -- there's no card-carrying membership that says, I'm part of this club. I'm the one who did this, and here is my address and phone number.
So, really, what they did to Gawker was come in behind the scenes in the past few weeks, past few months, figure out vulnerabilities, and essentially start to take the keys to the kingdom. Everything that Gawker held dear, most important, the user information, they took all of that out and splayed it out across the Internet.
They didn't hide the information for themselves for some sort of kind of nefarious means. They said, here, take it, because this is really -- they're the crown jewels for a website.
----
JEFFREY BROWN: Now, how are those people affected, in what ways?
HARI SREENIVASAN: Well, so, the thing -- it kind of gets back to a little bit of social engineering.
So a lot of times people don't make separate passwords and separate usernames for different websites. Sometimes, they use the same website or same e-mail address that I have for work on to a site like Gawker, and then maybe that's the same password that gets me into Facebook, and then it's also connected to Twitter.
So, as we see all of these different kind of communities that we participate in during the day, people aren't very good at keeping these walls separate. So, that's where the real influence is.
Bold-blue emphasis mine
Labels:
networking,
pc security,
web
Monday, September 20, 2010
SECURITY - The Bad Idea From Intel
"Intel's walled garden plan to put A/V vendors out of business" by Jon Stokes, Ars Technica 9/14/2010
Of course, my post title is my own opinion of this idea (note my bold-blue highlight above).
In describing the motivation behind Intel's recent purchase of McAfee for a packed-out audience at the Intel Developer Forum, Intel's Paul Otellini framed it as an effort to move the way the company approaches security "from a known-bad model to a known-good model." Otellini went on to briefly describe the shift in a way that sounded innocuous enough--current A/V efforts focus on building up a library of known threats against which they protect a user, but Intel would love to move to a world where only code from known and trusted parties runs on x86 systems. It sounds sensible enough, so what could be objectionable about that?
Depending how enamored you are of Apple's App Store model, where only Apple-approved code gets to run on your iPhone, you may or may not be happy in Intel's planned utopia. Because, in a nutshell, the App Store model is more or less what Intel is describing. Regardless of what you think of the idea, its success would have at least two unmitigated upsides: 1) everyone will get vPro by default (i.e., it seems hard to imagine that Intel will still charge for security as an added feature), and 2) it would put every security company (except McAfee, of course), out of business. (The second one is of course a downside for security vendors, but it's an upside for users who despise intrusive A/V software.)
From a jungle to an ecosystem of walled gardens
For a company that made its fortune on the back of the x86 ISA, the shift that Intel envisions is nothing less than tectonic. x86 became the world's most popular ISA in part because anything and everything could (and eventually would) run on it. And don't forget Microsoft's role in all of this—remember the "Wintel" duopoly of years gone by? Like x86, Windows ended up being the default OS for the desktop software market, and everything else was niche. And, like x86, Windows spread because everyone who wanted it could get it and run anything they wanted on it.
The fact that x86 was so popular and open gave rise to today's A/V industry, where security companies spend 100 percent of their effort trying to identify and thwart every conceivable form of bad behavior. This approach is extremely labor-intensive and failure-prone, which the security companies love because it keeps them in business.
What Intel is proposing is that the entire x86 ecosystem move to the opposite approach, and run only the code that has been blessed as safe by some trusted authority.
Now, there are a few ways that this is likely to play out, and none of these options are mutually exclusive.
One way should be clear from Intel's purchase of McAfee: the company plans to have two roles as a security provider: a component provider role, and an end-to-end platform/software/services provider role. First, there's the company's traditional platform role, where Intel provides OEMs the basic tools for building their own walled gardens. Intel has been pushing this for some time, mainly in its ultramobile products. If anyone is using Intel's ingredients (an app store plus hardware with support for running only signed code) to build their own little version of the App Store ecosystem, it's probably one of the European or Asian carriers that sells rebadged Intel mobile internet devices (MIDs). It's clear that no one is really doing this on the desktop with vPro, though.
Then there's the McAfee purchase, which shows that Intel plans to offer end-to-end security solutions, in addition to providing the pieces out of which another vendor can build their own. So with McAfee, Intel probably plans to offer a default walled garden option, of sorts. At the very least, it's conceivable that Intel could build its own secure app store ecosystem, where developers send code to McAfee for approval and distribution. In this model, McAfee would essentially act as the "Apple" for everyone making, say, MeeGo apps.
In the world described above, the x86 ecosystem slowly transitions from being a jungle to network of walled gardens, with Intel tending one of the largest gardens. If you're using an x86-based GoogleTV, you might participate in Google's walled garden, but not be able to run any other x86 code. Or, if you have an Intel phone from Nokia, you might be stuck in the MeeGo walled garden.
A page from the Web
None of the walled garden approaches described above sound very attractive for the desktop, and they'll probably be rejected outright by many Linux and open-source users. But there is another approach, one which Intel might decide to pursue on the desktop. The company could set up a number of trusted signing authorities for x86 code, and developers could approach any one of them to get their code signed for distribution. This is, of course, the same model used on the Web, where e-commerce sites submit an application for an https certificate.
This distributed approach seems to work well enough online, and I would personally be quite happy to use it on all my PCs. I would also love to hear from users who object to this approach—please jump into the comments below and sound off.
Pick any two
Obviously, security has always been a serious problem in the wild and woolly world of x86 and Windows. This is true mainly because Wintel is the biggest animal in the ecosystem, so bad actors get the most bang for their buck by targeting it. So why has Intel suddenly gotten so serious about it that the company is making this enormous change to the very nature of its core platform?
The answer is fairly straightforward: Intel wants to push x86 into niches that it doesn't currently occupy (phones, appliances, embedded), but it can't afford to take the bad parts along for the ride. Seriously, if you were worried about a particular phone or TV being compromised, you just wouldn't buy it. Contrast this to the Windows desktop, which many users may be forced to use for various reasons.
So Intel's dilemma looks like this: open, secure, ubiquitous—pick any two, but given the economics of the semiconductor industry, "ubiquitous" has to be one of them. Open and ubiquitous have gotten Intel where it is today, and the company is betting that secure and ubiquitous can take it the rest of the way.
Of course, my post title is my own opinion of this idea (note my bold-blue highlight above).
Labels:
networking,
pc security,
win xp,
windows
Monday, March 1, 2010
NETWORKING - US Behind in Broadband
The following is very sad considering we invented the internet in 1958.
"Advanced Research Projects Agency (ARPA or DARPA) in February 1958"
"US Broadband Figures Show 40 Percent Lack High-Speed Internet: STUDY" by JOELLE TESSLER, Huffington Post 2/16/2010
"Advanced Research Projects Agency (ARPA or DARPA) in February 1958"
"US Broadband Figures Show 40 Percent Lack High-Speed Internet: STUDY" by JOELLE TESSLER, Huffington Post 2/16/2010
Roughly 40 percent of Americans do not have high-speed Internet access at home, according to new Commerce Department figures that underscore the challenges facing policymakers who are trying to bring affordable broadband connections to everyone.
The Obama administration and Congress have identified universal broadband as a key to driving economic development, producing jobs and bringing educational opportunities and cutting-edge medicine to all corners of the country.
"We're at a point where high-speed access to the Internet is critical to the ability of people to be successful in today's economy and society at large," said Larry Strickling, head of the National Telecommunications and Information Administration (NTIA), an arm of the Commerce Department that released the data Tuesday.
The NTIA and the Rural Utilities Service, part of the Agriculture Department, are in the middle of handing out $7.2 billion in stimulus funding for broadband. Most of that money will be used to build networks in parts of the country that lack high-speed Internet access.
And next month, the Federal Communications Commission will deliver policy recommendations to Congress on how to make universal broadband a reality. Among other things, the FCC is expected to propose expanding the fund that subsidizes telephone service in poor and rural communities, finding more airwaves for wireless broadband services and modernizing the FCC's rural telemedicine program to bring thousands of health clinics online.
FCC Chairman Julius Genachowski said Tuesday he wants 100 million U.S. households to have access to ultra high-speed Internet connections, with speeds of 100 megabits per second, by 2020. That would be several times faster than the download speeds many U.S. homes with broadband get now – 3 megabits to 20 megabits per second.
Genachowski also wants the U.S. to test even higher broadband speeds. One such testbed network could come from Google Inc., which said last week it plans to build a few experimental fiber-optic networks that would deliver 1 gigabit per second to as many as 500,000 Americans. That would be 10 times faster than a 100 megabit-per-second connection.
The NTIA report released Tuesday offers a snapshot of the current broadband landscape. It stems from a Census Bureau survey of about 54,000 households conducted in October of last year.
The statistics show that U.S. broadband usage continues to grow, with 64 percent of U.S. households subscribing to high-speed Internet as of October, up from 51 percent two years earlier.
Story continues below
But the results also highlight remaining hurdles, particularly in rural America. While 66 percent of urban households subscribed to broadband in October, that was true for only 54 percent of rural households, the survey found.
That is partly because broadband is not as widely available in rural areas. The phone and cable companies that provide the bulk of broadband connections in the U.S. have been slower to build high-speed systems in places that are too sparsely populated to justify the costly network investments.
Lack of broadband availability is only part of the challenge for Washington, however – because even in places where broadband is available, not everyone subscribes. Among households that do not have broadband, the survey found, 38 percent said they don't need it or are not interested. Twenty-six percent said it is too expensive. Only 3.6 percent said they do not subscribe because it is not available where they live.
For policymakers, Strickling said, this means that helping people see "what they are missing" is another important piece of the puzzle. Last year's stimulus bill set aside at least $250 million for broadband adoption programs to teach people computer and Internet skills and ensure they have the equipment to get online.
Other key survey findings include:
_ 89 percent of Americans with an annual household income greater than $150,000 used a broadband connection at home in October, compared with 29 percent of Americans with a household income less than $15,000.
_ 67 percent of Asian Americans and 66 percent of Caucasians used broadband at home in October, compared with 46 percent of blacks and 40 percent of Hispanics.
_ Home broadband usage was highest among people aged 18 to 24, at 81 percent, and lowest among people 55 and older, at 46 percent.
Labels:
computers,
networking
Monday, February 22, 2010
WINXP - Cannot Disable Network Connections
I had a problem after the 2/10/2010 Microsoft Updates, I could NOT disable my Network Connection.
At home I normally disable/enable my Network Connection to provide increased security since I do not have a need to be online most of the time.
Note that this problem MAY not be caused by the updates themselves, since they did not cause this problem at work.
Disable Connection Error Dialog
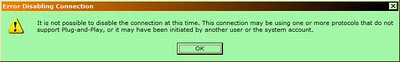 (click for larger view)
(click for larger view)
I did find a fix via Google, rebuild of CatRoot2 folder, steps are....
Hope this works if you have this problem.
At home I normally disable/enable my Network Connection to provide increased security since I do not have a need to be online most of the time.
Note that this problem MAY not be caused by the updates themselves, since they did not cause this problem at work.
 (click for larger view)
(click for larger view)I did find a fix via Google, rebuild of CatRoot2 folder, steps are....
- Boot to Safe Mode (no networking)
- Open Command Prompt, enter
net stop cryptsvc
and close dialog when stopped - Goto C:\WINDOWS\system32\CatRoot2
WARNING - NOT folder CatRoot - Rename folder CatRoot2 -> OLDCatRoot2
- Reboot normally (forces rebuild of CatRoot2)
- If you can disable/enable Network Connections, you can delete folder OLDCatRoot2
Hope this works if you have this problem.
Labels:
networking,
windows,
winxp
Thursday, March 5, 2009
WINXP - Broken Bookmarks, DeadLinks
How many times have we tried to go to a Favorites' link (aka URL) and got an error. This is sometimes called a Dead Link. There are tools that can verify/check your Favorites folder and verify the links.
The one I just found is AM-DeadLinks (freeware)
Some features: (use screenshot below for clarification)
Depending on how many links you have in Favorites, AM-DeadLinks will take a long time to scan all entries in the normal mode, and noticeably longer in the FavIcon mode.
In the screenshot, in the bottom Statusbar, note that I had 1916 Bookmarks, which took a good 10-15min to scan (at work using T1 broadband). Also note the Connections: 10, which means this tool is fast but uses much bandwidth. Therefore I suggest you run this tool with NO other windows open, especially a WEB Browser.
Just like any WinXP window with columns, if you click one (like Status) the display box will sort by the contents of the column. Clicking the Status column will put broken links at the top. And right-clicking a broken link brings up a Context Menu with options.
Check it out.
AM-DeadLinks Dialog
(click to enlarge)

The one I just found is AM-DeadLinks (freeware)
Some features: (use screenshot below for clarification)
- Two modes of scanning and verifying links
- Normal which only verifies links
- FavIcons scan which verifies links AND downloads site icons
- From the dialog, you can:
- Edit link Properties (aka change name or URL)
- Delete the link if it is broken
- Launch the link in a dialog browser or change to full-screen browser
Depending on how many links you have in Favorites, AM-DeadLinks will take a long time to scan all entries in the normal mode, and noticeably longer in the FavIcon mode.
In the screenshot, in the bottom Statusbar, note that I had 1916 Bookmarks, which took a good 10-15min to scan (at work using T1 broadband). Also note the Connections: 10, which means this tool is fast but uses much bandwidth. Therefore I suggest you run this tool with NO other windows open, especially a WEB Browser.
Just like any WinXP window with columns, if you click one (like Status) the display box will sort by the contents of the column. Clicking the Status column will put broken links at the top. And right-clicking a broken link brings up a Context Menu with options.
Check it out.
(click to enlarge)

Labels:
networking,
windows,
winxp
Tuesday, February 24, 2009
WINXP - Networking, Checking Your Connection
On my previous post I mentioned the ping command, then realized I haven't addressed this issue. So here goes.
There are many tools to check/test your network connection. The best would be those provided by your ISP or manufacturer of your Router/Modem. Having said that, one of the simplest and easiest is WinXP's ping command.
All you need to do is open the Command Prompt ([Start], Programs, Accessories). I suggest you COPY the shortcut to your Quick Launch toolbar. The following screenshots (click for larger view) is all you need to use this to test your network connection.
The command syntax = ping domain_or_IP
 Ping IP
Ping IP
OR
 Ping Domain
Ping Domain
Note that ping domain is an easy way to test a specific site.
IMPORTANT: Take special note on Firewall settings in the previous article. You cannot ping a local network IP if the Firewall, Exceptions are not set properly.
Tools:
One tool/utility I can recommend (I use at work and home) is GEO Spider.
See the screenshots on their WEB site and note the requirements. (NET Framework 2.0 including download link).
There are many tools to check/test your network connection. The best would be those provided by your ISP or manufacturer of your Router/Modem. Having said that, one of the simplest and easiest is WinXP's ping command.
All you need to do is open the Command Prompt ([Start], Programs, Accessories). I suggest you COPY the shortcut to your Quick Launch toolbar. The following screenshots (click for larger view) is all you need to use this to test your network connection.
The command syntax = ping domain_or_IP
 Ping IP
Ping IPOR
 Ping Domain
Ping DomainNote that ping domain is an easy way to test a specific site.
IMPORTANT: Take special note on Firewall settings in the previous article. You cannot ping a local network IP if the Firewall, Exceptions are not set properly.
Tools:
One tool/utility I can recommend (I use at work and home) is GEO Spider.
See the screenshots on their WEB site and note the requirements. (NET Framework 2.0 including download link).
Labels:
networking,
windows,
winxp
Monday, February 23, 2009
WINXP - Networking, Shares
This is some info on Sharing Folders or Printers with other Desktops on a network, at home or in a business. This discussion assumes you have your network already setup and running.
To share a folder, right-click the folder in Explorer (aka My Computer), and select Properties, Sharing tab. By default WinXP has Network sharing and security DISABLED, so you will first have to enable sharing by using the If you understand the risks... option.

After a few [Next] clicks, you get the Enable File Sharing dialog. I highly suggest the Just enable file sharing option as the simplest.

After enabling File Sharing, you get the Dialog that will normally open when you right-click on a folder and selecting Properties, Sharing tab. (so you enable sharing once)

Now you can click the Share this folder on the network option, then [Apply]. That's all you really need. You close all dialogs.
For Sharing Printers, if you have already enabled sharing, you just use Printers and Faxes dialog and right-click the printer you want to share, select Properties. Sharing tab.

IMPORTANT: Firewall Setting
There is a Firewall option that must be enabled to allow sharing of your folders or printers that MAY not automatically be set.
You can use Control Panel, Windows Firewall icon, Exceptions tab. You must enable (check) File and Printer Sharing.

There is another side effect if you DO NOT have this exception enabled; you can use the ping command to ping other desktops on your network, but they will NOT be able to ping you.
To share a folder, right-click the folder in Explorer (aka My Computer), and select Properties, Sharing tab. By default WinXP has Network sharing and security DISABLED, so you will first have to enable sharing by using the If you understand the risks... option.

After a few [Next] clicks, you get the Enable File Sharing dialog. I highly suggest the Just enable file sharing option as the simplest.

After enabling File Sharing, you get the Dialog that will normally open when you right-click on a folder and selecting Properties, Sharing tab. (so you enable sharing once)

Now you can click the Share this folder on the network option, then [Apply]. That's all you really need. You close all dialogs.
For Sharing Printers, if you have already enabled sharing, you just use Printers and Faxes dialog and right-click the printer you want to share, select Properties. Sharing tab.

IMPORTANT: Firewall Setting
There is a Firewall option that must be enabled to allow sharing of your folders or printers that MAY not automatically be set.
You can use Control Panel, Windows Firewall icon, Exceptions tab. You must enable (check) File and Printer Sharing.

There is another side effect if you DO NOT have this exception enabled; you can use the ping command to ping other desktops on your network, but they will NOT be able to ping you.
Labels:
networking,
windows,
winxp
Friday, September 19, 2008
COMPUTERS - Networking
The biggest growth in computing has been networking, specifically the World Wide Web (WWW or WEB).
Is there anyone in the industrialized world who have not heard at least one of the terms Google, Amazon.COM, eBay, YaHoo, Facebook. Then there's all the referenced on TV problems about "visit our WEB site."
How many business have made the WEB a part of how they do business? I can shop at Albert son's or Vons for groceries on the WEB.
WHAT MAKES UP NETWORKING AND THE WWW
What is a Network in the context of computers? I could go into a long winded explanation but Wikipedia's Computer Network article has it all.
The following are quotes from the article on WWW:
Most users are aware of how networking operates even though details may not be known. Most users of Windows now of Internet Explorer (IE) browser, but be unaware of all the details on how it works. So here's my minimalist information on Networking on a PC.
About email Servers:
Is there anyone in the industrialized world who have not heard at least one of the terms Google, Amazon.COM, eBay, YaHoo, Facebook. Then there's all the referenced on TV problems about "visit our WEB site."
How many business have made the WEB a part of how they do business? I can shop at Albert son's or Vons for groceries on the WEB.
WHAT MAKES UP NETWORKING AND THE WWW
What is a Network in the context of computers? I could go into a long winded explanation but Wikipedia's Computer Network article has it all.
The following are quotes from the article on WWW:
"The underlying ideas of the Web can be traced as far back as 1980, when, at CERN in Switzerland, Tim Berners-Lee built ENQUIRE (referring to Enquire Within Upon Everything, a book he recalled from his youth). While it was rather different from the system in use today, it contained many of the same core ideas (and even some of the ideas of Berners-Lee's next project after the World Wide Web, the Semantic Web)."
"In March 1989, Tim Berners-Lee wrote a proposal,[2] which referenced ENQUIRE and described a more elaborate information management system. With help from Robert Cailliau, he published a more formal proposal for the World Wide Web on November 12, 1990.[3] The role model was provided by EBT's (Electronic Book Technology, a spin-off from the Institute for Research in Information and Scholarship at Brown University) Dynatext SGML reader that CERN had licensed. The Dynatext system was considered, however technically advanced (a key player in the extension of SGML ISO 8879:1986 to Hypermedia within HyTime), too expensive and with an inappropriate licensing policy for general HEP (High Energy Physics) community use: a fee for each document and each time a document was charged."
"On April 30, 1993, CERN announced[8] that the World Wide Web would be free to anyone, with no fees due. Coming two months after the announcement that the Gopher protocol was no longer free to use, this produced a rapid shift away from Gopher and towards the Web. An early popular Web browser was ViolaWWW, which was based upon HyperCard."
"Scholars generally agree, however, that the turning point for the World Wide Web began with the introduction[9] of the Mosaic Web browser[10] in 1993, a graphical browser developed by a team at the National Center for Supercomputing Applications at the University of Illinois at Urbana-Champaign (NCSA-UIUC), led by Marc Andreessen. Funding for Mosaic came from the High-Performance Computing and Communications Initiative, a funding program initiated by then-Senator Al Gore's High Performance Computing and Communication Act of 1991, also known as the Gore Bill.[11] (See Al Gore's contributions to the Internet and technology for more information.) Prior to the release of Mosaic, graphics were not commonly mixed with text in Web pages, and its popularity was less than older protocols in use over the Internet, such as Gopher and Wide Area Information Servers (WAIS). Mosaic's graphical user interface allowed the Web to become, by far, the most popular Internet protocol."
"The World Wide Web Consortium (W3C) was founded by Tim Berners-Lee after he left the European Organization for Nuclear Research (CERN) in October, 1994. It was founded at the Massachusetts Institute of Technology Laboratory for Computer Science (MIT/LCS) with support from the Defense Advanced Research Projects Agency (DARPA) -- which had pioneered the Internet -- and the European Commission."
Most users are aware of how networking operates even though details may not be known. Most users of Windows now of Internet Explorer (IE) browser, but be unaware of all the details on how it works. So here's my minimalist information on Networking on a PC.
- You physically connect to a Network (and thereby the WWW) via Dial-Up or Local Area Network (LAN) connection in your PC.
- Dial-Up = a card/adapter that uses a normal phone line, and tones (like in Touch-Tone) to talk or pass data to your Internet Service Provider (ISP).
- LAN = a card/adapter that uses Ethernet technology to communicate, and uses Packets protocols to send data.
- Packets are a much faster way to send data, especially when using fiber optic cables. This has also become what our modern digital phone system uses because one fiber optic line can carry multiple-thousands of calls.
- Your LAN cable usually connects to a Cable/DSL Modem or Router, and from there to your ISP.
- For both types of connection, your ISP will tell you how to setup to communicate with their systems (Computer Servers). Most ISPs also provide your email service (email Servers), and include hard drive space on their system for publishing your Web Pages or as a dropbox (a location where you can share files with others, drop files into a "box").
About email Servers:
- Most ISPs use POP/SMTP email Servers. These type of servers use a special Internet Protocol (IP), TCP Ports specification for email services. They hold your "mailbox." A POP Server is where you download your email from. A SMTP Server is where you send your email to.
- Another type of email server is represented (by example) by a Microsoft Exchange Server. Many companies use this, or similar servers, for email because it has advantages; like being able to keep your email profile (Outlook account & settings, email files, etc.) on the Exchange Server, which means you can logon to your email account from any PC without having to setup the account on that PC first.
Labels:
computers,
networking,
win7,
windows,
winxp
Subscribe to:
Posts (Atom)




